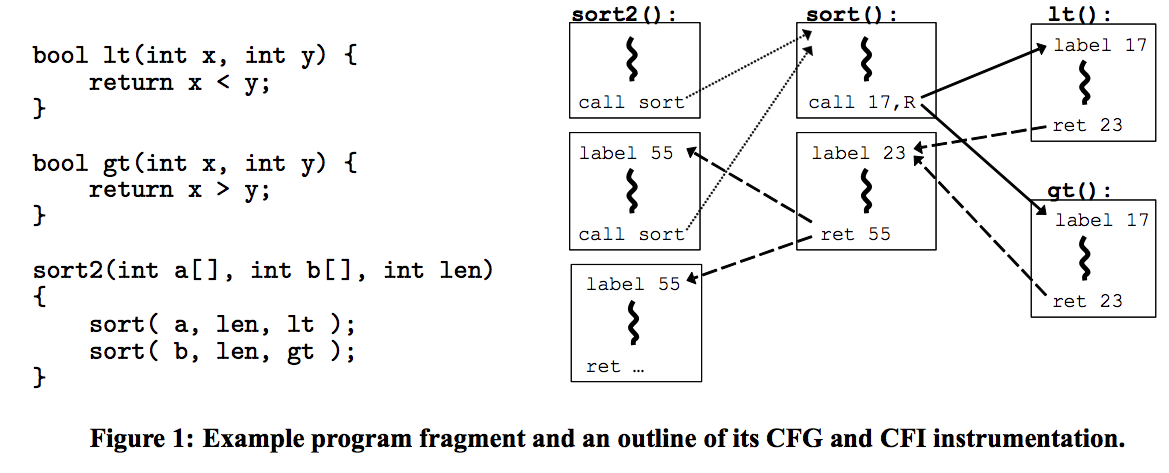
Control Flow Integrity
According to M. Abadi et al. in there paper, the control flow integrity (CFI) security dictates that software execution must follow a path of a Control-Flow Graph (CFG) determined ahead of time. The below figure shows a method to enforce the CFI.